Cyber Security Awareness - An Overview
Table of ContentsThe 8-Second Trick For Cyber Security AwarenessFacts About Cyber Security Awareness RevealedCyber Security Awareness for BeginnersFacts About Cyber Security Awareness RevealedSome Ideas on Cyber Security Awareness You Need To Know
Aside from work experience and university degrees, some employers additionally prefer job prospects that have gotten qualifications showing their understanding of ideal methods in the field. There are also a lot more specific certificates, which can highlight specialized knowledge of computer style, engineering or management.It is usually contrasted with physical safety and security, which is the more traditional security method intended at regulating accessibility to structures and also other objects in the actual world., and in some cases physical and online security are signed up with with each other in the org graph under the same executive, cyber protection concentrates on safeguarding properties from harmful logins and also code, not break-ins.
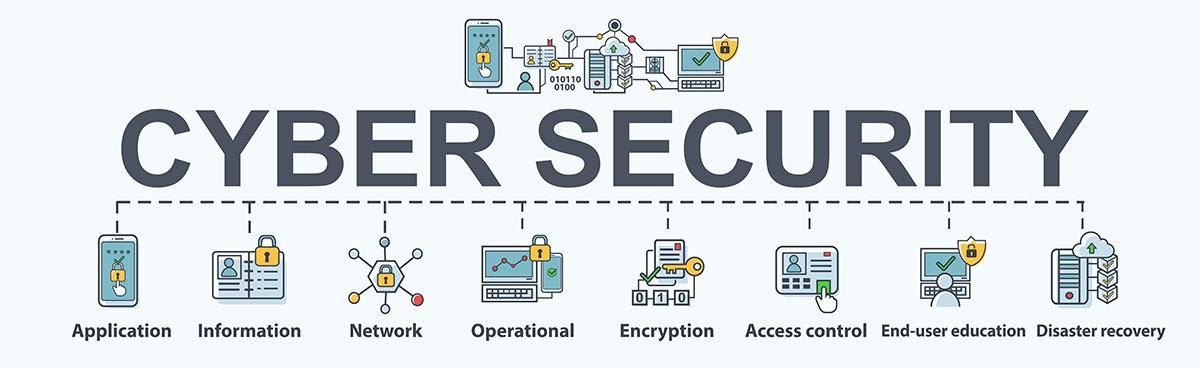
There are a variety of ways to break down the various types Kapersky Labs has one schema, Mindcore an additional but below are one of the most popular types you'll read about: prevents and also secures versus unauthorized invasion right into company networks makes applications a lot more safe by discovering and also dealing with susceptabilities in application code sometimes likewise described as keeps data safeguard from unapproved accessibility or changes, both when it's being kept as well as when it's being transmitted from one equipment to one more commonly shortened as is a process by which companies assess as well as safeguard public data concerning themselves that could, if correctly examined and also grouped with various other data by a creative enemy, disclose a bigger picture that should remain concealed Some elements of are likewise taken into consideration to lie under the cyber security umbrella; specifically, methods to remediate extensive data loss or service outages as a result of a cyber assault are component of the larger cyber protection discipline Each of the kinds of cyber safety combat cyber safety threats within a specific conceptual world (Cyber Security Awareness).
Some Of Cyber Security Awareness
Both HIPAA and GDPR, for example, have comprehensive cyber safety structures mandating particular treatments firms covered by the laws need to follow. Obviously, the majority of online safety and security frameworks are not obligatory, even ones established by governments. Among one of the most preferred of these is NIST's Cybersecurity Structure, version 1. 1 of which was launched in April of 2018.
These real duties can differ widely from business to company, so it's crucial to take a better look at each task separately to recognize it. At the very leading of the food web is the Principal Details Gatekeeper, or CISO, find though even that title isn't uncompromising.
Safety leaders have shouldered their method right into the C-suite and conference rooms, as safeguarding firm data comes to be objective important for companies., as well as you'll acknowledge that they tie right into the kinds of cyber safety and security we detailed above.
Unknown Facts About Cyber Security Awareness

This was particularly real as cyber security took a while to emerge as a distinct self-control; lots of departments established de facto safety and security pros from within, contemporary of individuals that had an interest in the subject. Nevertheless, as is additionally real of lots of elements of IT today, cyber safety has actually come to be a growing number of professionalized, as well as lots of college programs and even majors have emerged to prepare potential cyber safety and security staff.
The information of cyber safety tasks are, like any type of state-of-the-art job, constantly altering, as well as the secret to continuing success is to keep learning and remain adaptable: as protection evangelist Roger Grimes puts it, "re-invent your skills every five to 10 years."One way, though certainly not the only means, to demonstrate that you're staying on top of the industry is to go after some cyber security certifications.
The smart Trick of Cyber Security Awareness That Nobody is Talking About
It is beyond the extent of this record to present all cyber capabilities that danger actors might release. Below is a nonexhaustive checklist of usual devices and methods that are utilized by danger actors. For simplicity, they are listed alphabetically as well as are not placed according to regularity or influence.
2 usual code shot techniques are as well go right here as. XSS is a code injection technique whereby a risk star injects and performs harmful code within an internet application by bypassing the systems that verify input. The malicious code is performed in the internet browser of individuals accessing the made use of web application. Code injected by XSS might either be a single execution or stored for future usage.
Cyber Security Awareness Fundamentals Explained
g., by means of LDAP or Energetic Directory Site) to make sure that controls can be provided from one system rather than spread throughout numerous private systems. For the several clinical tools that are auto-logon and also in constant use, various other sorts the original source of accessibility controls can be established such as preshared tricks and/or MAC address verification.